
Exploring the Intricacies and History of Onion Routing
this previous article, we explored the history of the dark web including a few notable incidents that have occurred on the dark web. In today’s article, we’ll be looking at some of the technology behind onion routing as well as trying to explain how it works effectively. While today’s article might be a touch theory-heavy, we’ll try to keep it at a minimum for now.
What is Onion Routing
Best known as a technique for applying anonymity strategies to browsing, onion routing provides a way for this to occur by applying layers of encryption and routing the traffic through the network for privacy reasons. While it isn’t foolproof it has provided many benefits over traditional web browsing.
First experimented with at the United States Naval Academy, Onion Routing remained the domain of government-only employees before being released into the wild for anyone to use.
When it was first released, it was reasonably secure, providing you acted within certain limitations that would help you protect your privacy. However as technology evolved and computing power grew with it, eventually some strategies and methods could be applied to help defeat the privacy-based focus of said routing.
Lastly, it is important to realise that TOR Is just one iteration of onion routing. While it’s probably the best-known of all protocols, there are others that accompany it.
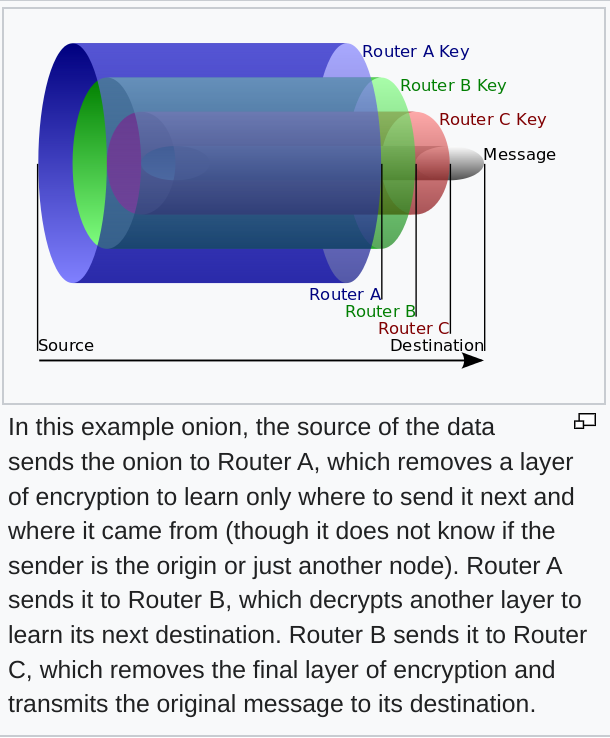 The principals of onion routing. Source: Wikipedia.How Does It Work
The principals of onion routing. Source: Wikipedia.How Does It Work
Like an onion, privacy-focused routing occurs in layers. There’s a Wikipedia visual above that helps understand the concept, but typically speaking each onion “layer” adds a level of encryption which is removed as the traffic is routed to and from its destination.
The privacy factor is added as each “layer” can only forward to the next, without knowing where the traffic is headed beyond that. Even better still, as the traffic passes through each node, the node prior is unable to tell if the traffic has originated from there or has come from somewhere else.
In the early days, this is what made TOR so effective. The fact that this new method applied these protections meant that mitigation didn’t really exist in the early days. While the tracking methods became more complex over time, it was still worthwhile for many users to route their traffic via TOR.
 TOX is a privacy-focused chat option. Source: WikipediaLimitations
TOX is a privacy-focused chat option. Source: WikipediaLimitations
With a traditional ISP, you’ll find that it’s easy to monitor traffic. This is due to many reasons outside the scope of a single article. Onion routing prevents this, but only to a point. Given it’s now a well-used and well-understood protocol, this means that strategies are available to mitigate it. While there are more than a few (including some that you’d expect are a matter of national security), here are a couple of the most common ones that can allow privacy on TOR to be compromised.
- End-to-End Timing Analysis:
Timing analysis can potentially compromise anonymity. Adversaries could analyze the timing of packets entering and exiting the onion routing network to correlate them and infer the source and destination.
2. End-Node Vulnerabilities:
If the entry or exit node in the onion routing network is compromised, the anonymity of the user may be compromised. Adversaries may be able to correlate the traffic entering or exiting the network. US intelligence agencies in particular are believed to use these types of vulnerabilities.
3. Exit Node Monitoring:
Since the traffic exits the onion routing network at the exit node, if the exit node is malicious or compromised, it could monitor or manipulate the unencrypted traffic, potentially compromising user privacy.
4. Risk of Malicious Nodes:
The system relies on the assumption that most nodes in the network are honest. If a significant number of nodes are controlled by malicious actors, they could compromise the integrity and security of the entire onion routing network. The previously mentioned US intelligence nodes could be considered to be malicious in that they monitor traffic that passes through them.
 After breaching the data, Snowdon fled to Russia. He remains there to this day. Source: Wikipedia.The Snowdon Leaks
After breaching the data, Snowdon fled to Russia. He remains there to this day. Source: Wikipedia.The Snowdon Leaks
It’s accurate to say that some of the more well-known data breaches were responsible for shining light on some of the ways that intelligence and state-backed agencies were able to leverage TOR for signals intelligence purposes. While the Snowdon leaks weren’t the only ones responsible for providing information about such surveillance programmes, they did allow us to draw deeper conclusions into why such programs existed as well as what they were targeting.
However, in performing these data leaks in 2013, TOR was a critical thread in bringing it all together. This allowed Snowdon to communicate anonymously while leaking the data. While TOR wasn’t the only strategy used in protecting anonymity it was a critical part of the link. In fact, depending on your requirements using TOR could be considered the only option, rather than simply another option.
Like government surveillance, data breaches are no joke. However, we do believe that being able to have privacy is in fact, a critical part of a functional society. We’ve even written about it before, in previous articles you can find in our history. We’re passionate about privacy-related issues, so feel free to share your own thoughts in the comments.
Final Words
As tech and cryptography evolve there may come a time when onion routing and the tor project in general are not fit for purposes in terms of providing an alternative, privacy-focused option.
Quantum computing and other strategies may influence cryptography and onion routing making it not viable in future, however, the advancement of AI-based systems means we have new ways to communicate for those that value that.
In a world full of web-based tracking, targeted advertising and ongoing data breaches, we think conversations around privacy and data ownership should occur more frequently. What do you think?
Medium has recently made some algorithm changes to improve the discoverability of articles like this one. These changes are designed to ensure that high-quality content reaches a wider audience, and your engagement plays a crucial role in making that happen.
If you found this article insightful, informative, or entertaining, we kindly encourage you to show your support. Clapping for this article not only lets the author know that their work is appreciated but also helps boost its visibility to others who might benefit from it.
?? Enjoyed this article? Support our work and join the community! ??
?? Support me on Ko-fi: Investigator515
?? Join our OSINT channel for exclusive updates or
?? Follow our crypto for the latest giveaways
?? Follow us on
We’re now on
?? Articles we think you’ll like:
- Signals From Space: The International Space Station
- Ukraine OSINT: Strava Strikes Again
?? Want more content like this? Sign up for email updates











